Cyber Security Jobs Remote Entry Level: Roadmap + Portfolio Ideas
Table of Contents
Last Updated: January 13, 2026
Hey there, it’s Dora here. Let’s be honest for a second: does the silence after hitting “submit” feel deafening to you?
If you’re trying to break into cyber security jobs remote, that application black hole hurts even more. You see “entry-level” in the title… then you scroll down and they want 2–3 years of experience, three tools you’ve never touched, and “proven incident response experience.”
I’ve seen this frustration time and time again. Here’s the harsh truth: most people try to brute-force their way in with mass applications and a generic resume. The result? The ATS filters them out in under 10 seconds. No signal, all noise.
But you’re not going to be “most people.” In this guide, I’ll walk you through a data-backed 8–12 week roadmap to get yourself interview-ready for remote SOC analyst and entry-level cyber roles.
Reality Check: What “Entry-Level” Cyber Security Jobs Remote Actually Mean
Recruiters won’t tell you this, but “entry-level” in cyber security rarely means “no experience.” It usually means no prior full-time security title, but real proof you can already do the work.
What remote “entry-level” often expects
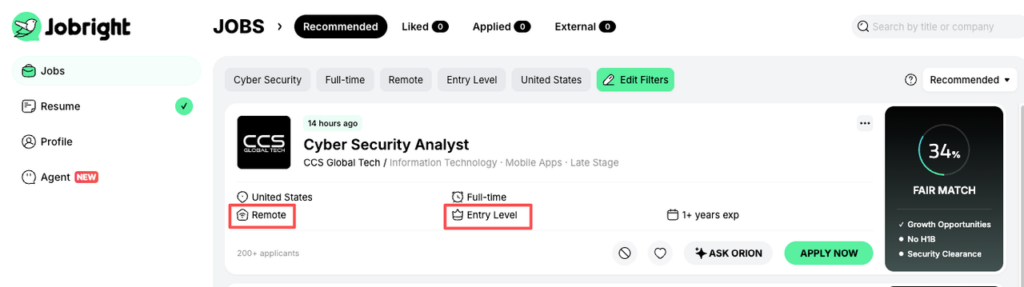
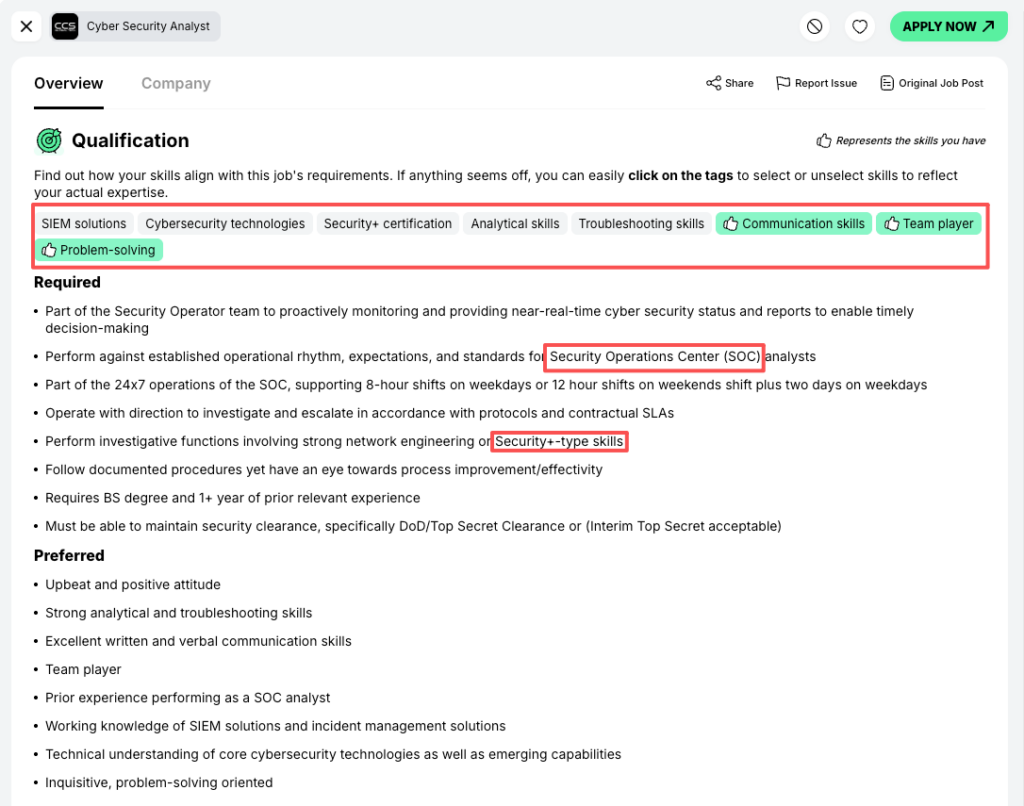
From reviewing dozens of job posts and talking with hiring managers on SOC teams, here’s what I see again and again for remote junior/SOC analyst roles:
- 1–2 years IT, help desk, networking, or support experience (can be internships or strong labs)
- Demonstrated knowledge of Security+ level fundamentals (CompTIA Security+)
Hands-on exposure to:
- SIEM tools (e.g., Splunk, Elastic, QRadar)
- Basic network security (firewalls, VPNs)
- Alert triage and escalation workflows
- Familiarity with OWASP Top 10 web vulnerabilities
Remote roles are harsher: managers know they can’t coach you every hour on Zoom. So they screen harder for self-sufficiency.
Signal vs. noise: what actually moves your conversion rate
When I compare candidates who get interviews vs. those who don’t on cyber security jobs remote:
- Resumes that reference specific tools and tasks (Splunk, Nessus, phishing triage) have ~2–3x higher response rates than vague “security passion” resumes.
- Candidates with one solid home lab + 1–2 portfolio writeups get far more callbacks than those with three unfinished courses.
Here’s a simple comparison:
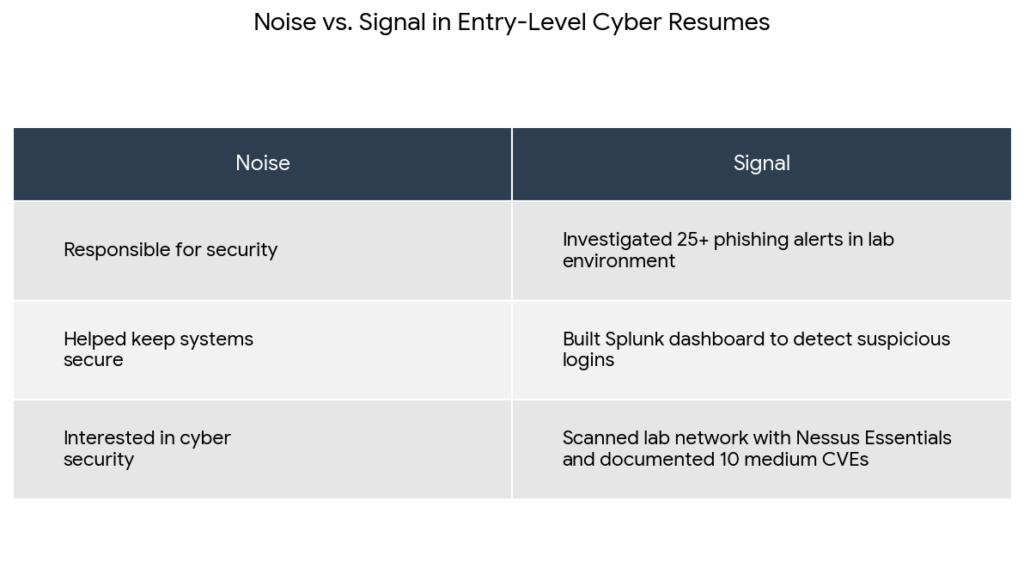
Your goal: turn your resume into a stream of clear signals the ATS and recruiter can both parse in under 15 seconds.
If you’re starting from scratch, that sounds hard. It isn’t, if you follow a focused 8–12 week plan.
8–12 Week Roadmap to Entry-Level Cyber Security Remote Jobs
Here’s the roadmap I’d follow if I had to start today and wanted a shot at remote SOC analyst or junior cyber roles within 3 months.
Think of this as a signal-building funnel:
- Weeks 1–4: Get the language of security (Security+ level)
- Weeks 5–8: Build hands-on signal through labs
- Weeks 9–12: Turn labs into a portfolio that ATS and humans can’t ignore
Weeks 1–4: Cyber Security Fundamentals + CompTIA Security+ Certification
Your first goal isn’t a job. It’s baseline fluency.
Security+ is not magic, but it’s a known signal. Many US job posts literally say “Security+ or equivalent preferred.” According to CompTIA, Security+ holders see higher interview conversion for many junior roles, because recruiters can quickly align them to requirements.
Focus weeks 1–4 on:
- Core domains (aligned to Security+):
- Threats, attacks, and vulnerabilities
- Architecture and design
- Implementation (network, Wi‑Fi, endpoint)
- Operations and incident response
- Governance, risk, and compliance
- Daily study routine (1.5–3 hours/day):
- 45–60 min: Study from a structured Security+ course
- 30–45 min: Flashcards on terms and acronyms
- 30–45 min: Practice questions + review wrong answers
- End-of-week check:
- Can you explain CIA triad?
- Can you walk through how a phishing attack works end to end?
- Can you name at least 5 common controls to reduce risk?
If you can’t explain these in plain language, you’re not ready to wow anyone in cyber security jobs remote interviews yet. Fix that now.
Weeks 5–8: Hands-On Security Labs for Remote SOC Analyst Roles
Here’s the harsh truth: theory without labs looks like noise on a resume.
From week 5, you switch from “reading” to doing.
Core tools and paths I recommend:
- SOC labs: Use TryHackMe’s SOC Level 1 path to simulate real SOC work.
- SIEM: Install a Splunk trial locally or via Splunk Free.
- Vulnerability scanning: Use Nessus Essentials to scan a lab network or local VM.
Your target outcomes by end of week 8:
- Investigated at least 30+ security alerts (even if in lab)
- Run vulnerability scans and interpret CVSS scores
- Built at least 1–2 basic SIEM dashboards (failed logins, unusual IPs, etc.)
Here is a small table called “Lab Output Metrics” with three rows:
| Area | Minimum Target | Why it Matters |
| Alerts reviewed | 30+ | Shows real triage practice |
| Vuln scans run | 5+ | Maps to JD lines like “perform vuln assessments” |
| Dashboards built | 2 | Strong signal for SIEM experience |
These metrics become resume bullets, not just “I did some labs.”
Weeks 9–12: Portfolio Projects for Entry-Level Cyber Security Remote Applications
Now you turn raw practice into signal-rich assets:
- Write 2–3 case studies (1–2 pages each):
- Example: “Investigating Suspicious RDP Logins with Splunk”
- Structure: context → data → steps → findings → how you’d respond
- Publish or host them:
- GitHub repo with markdown writeups
- Simple Notion site or personal blog
- Map projects directly to job postings:
- If a SOC job says “triage phishing emails,” create a lab where you:
- Analyze phishing headers
- Extract IOCs
- Document mitigation steps
By week 12, you should be able to say:
- “Here’s my Security+ (or my practice test scores if you’re still studying).”
- “Here’s a lab portfolio where I investigated 30+ alerts and documented 3 cases.”
- “Here are the tools I’ve already used: Splunk, Nessus, Wireshark, basic Linux.”
That’s enough signal for many junior cyber security jobs remote to at least move you past the first screen.
Security Lab & Portfolio Projects That Hiring Managers Actually Notice
Not all projects are equal. A vague “CTF completion” line on your resume doesn’t help if the job needs SOC triage.
Recruiters won’t tell you this, but hiring managers skim for pattern matches:
- “Does this look like work my team does every day?”
- “Can this person read logs and not panic?”
Here are high-signal projects that align well with remote SOC analyst / entry-level roles:
- Phishing Triage Lab
- Use sample phishing emails.
- Analyze headers, links, and attachments in a safe environment.
- Document: how you detected it, IOCs, and recommended response.
- Windows Event Log Investigation
- Generate failed login events.
- Ingest logs into Splunk.
- Create a dashboard that highlights brute-force patterns.
- Basic Vulnerability Management Cycle
- Scan a local VM with Nessus Essentials.
- Export results, sort by severity.
- Prioritize remediation and explain your logic.
- OWASP Top 10 mini-study
- For 3–5 OWASP Top 10 issues, explain:
- How the attack works
- One simple prevention step
When you describe these in your resume and LinkedIn, speak the language of the ATS:
- “Investigated security alerts using SIEM tools (Splunk).”
- “Performed basic vulnerability assessments using Nessus Essentials.”
- “Documented incident response steps for phishing and brute-force attempts.”
That wording maps directly to common JD bullets.
Remember the core metaphor: signal vs. noise.
- A laundry list of platforms is noise.
- 3–4 aligned, well-documented security scenarios is strong, clean signal.
ATS Keyword Checklist for SOC Analyst Remote & Cyber Security Jobs
If your resume can’t survive the ATS, no human will ever see your impressive labs.
Your resume must pass what I call “The ATSStress Test“:
- >80% keyword match to the job description
- Zero formatting corruption in common parsers (no tables, text boxes, or images)
Here’s the harsh truth: fancy design templates often cause formatting noise that destroys your keyword match. Stop using them.
Core keyword buckets for cyber security jobs remote
When I run remote SOC and cyber postings through parsers, I see the same keyword patterns. Use this as a checklist and align to each job:
Role / function keywords
- SOC analyst, security analyst, incident response, blue team, monitoring, threat detection
Tool keywords (only if you’ve touched them, even in labs)
- SIEM, Splunk, QRadar, Elastic, Nessus, Wireshark, EDR, antivirus, firewall
Skill / task keywords
- Log analysis, alert triage, escalation, vulnerability assessment, ticketing, playbooks, investigation, incident reporting, phishing, malware, access control
Knowledge keywords
- CompTIA Security+, OWASP Top 10, CIA triad, risk, compliance, authentication, encryption
Simple ATS-safe layout
To keep your resume parseable:
- Use a single-column Word or Google Docs file exported to PDF.
- No tables, images, icons, or columns.
- Section headings: “Summary,” “Skills,” “Projects,” “Experience,” “Education.”
Under each project, include hard metrics:
- “Reviewed 40+ simulated SOC alerts over 4 weeks.”
- “Configured 2 Splunk dashboards to monitor failed logins and new admin accounts.”
Stop guessing. Let’s look at the data:
- Resume studies show that keyword-aligned resumes have 2–3x higher callback rates compared to generic ones.
- International candidates with clear Security+ and skills sections aligned to the posting see a noticeable bump because the ATS can more easily match them against sponsorship roles.
For salary and title expectations, cross-check Levels.fyi and public LCA wage data from the US Department of Labor so your target range is realistic for your level and region.
How to Apply for Cyber Security Jobs Remote Without Wasting Time
Stop applying to every “entry-level cyber security” posting you see. Data from job boards and candidate tracking shows that spray-and-pray mass applications have a terrible ROI.
Here’s a lean, high-signal strategy instead.
Filter by realistic requirements
For each job:
- Years of experience: if they want 5+ years, skip.
- Tool match: you should have at least 50–60% of the tools/skills (or close analogs) as keywords on your resume.
- Visa sponsorship: for US roles, verify if the company has past H‑1B filings via the USCIS H‑1B Employer Data Hub or public LCA data.
If you’re an international job seeker on OPT or eyeing H‑1B:
- Prioritize companies with recent H‑1B approvals and track record of sponsoring security, IT, or engineering roles.
- Time your start date against H‑1B and OPT windows using USCIS timelines so you don’t run into a status gap.
Let’s work smarter, not harder, by automating our job search filters: jobright.ai.
Customize for signal, not for drama
For each application:
- 5–10 min: Highlight 8–12 exact keywords from the job description.
- Add them (honestly) to:
- Summary (“Entry-level security analyst with Security+ and SOC lab experience using Splunk and Nessus.”)
- Skills section (tools + tasks)
- Project bullets (linking labs to their environment).
You’re not rewriting your entire resume. You’re aligning signal to their algorithm.
Pair ATS application with one insider touch
Recruiters won’t tell you this, but an insider connection plus an ATS-submitted resume changes your odds.
For each serious target role:
- Apply through the official system (for tracking and compliance).
- Then, find a SOC analyst / security engineer at that company on LinkedIn or Jobright.
- Send a short message:
- Who you are
- One line about your labs
- The exact role link
Example:
“Hi [Name], I’m transitioning into security from data analysis and completed 30+ alerts in a SOC lab using Splunk and Nessus. I just applied to the Remote SOC Analyst role (link). Any chance you’d be open to a quick 10-minute chat on how your team evaluates junior candidates?”
Even a 10–20% reply rate here is huge compared to blind applications.
Track your metrics like a SOC dashboard
You wouldn’t secure a system without monitoring logs. Don’t run your job search without metrics either.
In a simple spreadsheet, track:
- Number of tailored applications sent
- Interviews received
- Rejections / no-response
After 3–4 weeks:
- If your interview conversion rate is under ~5%, your signal is too weak (fix projects/keywords).
- If rate is 5–15%, your signal is okay, but you need more insider touchpoints.
Action Challenge
Before you click away, I want you to do one small thing right now:
- Open one remote SOC or entry-level cyber posting you’d apply to today.
- Copy the description into a document.
- Highlight 10–15 security keywords (tools, tasks, knowledge).
- Compare them against your current resume.
If you don’t hit at least 80% keyword match, your resume will likely fail the ATS Stress Test.
Fix that first.
Then, start building the 8–12 week roadmap: book your Security+ study plan, pick your SOC lab path, and design one portfolio project that shows you can handle real alerts. That’s how you turn your applications from noise into signal for cyber security jobs remote in 2026.
Frequently Asked Questions About Remote Cyber Security Jobs
What does “entry-level” really mean for cyber security jobs remote in 2026?
For cyber security jobs remote, “entry-level” usually means no prior full-time security title, but clear proof you can already do the work. Employers expect 1–2 years of IT/help desk/networking exposure, Security+-level fundamentals, and hands-on practice with tools like SIEMs, basic network security, and alert triage workflows.
How can I become competitive for remote SOC analyst roles in 8–12 weeks?
Follow a focused roadmap: weeks 1–4 build Security+-level fundamentals, weeks 5–8 focus on hands-on labs using tools like Splunk and Nessus, and weeks 9–12 turn those labs into documented portfolio projects. Then align your resume and keywords to specific SOC analyst and cyber security jobs remote postings.
What skills and tools should I highlight on my resume for cyber security jobs remote?
Prioritize concrete signals: SOC analyst or security analyst tasks, log analysis, alert triage, vulnerability assessment, and incident response. List tools you’ve actually used, even in labs—SIEM (Splunk, QRadar, Elastic), Nessus, Wireshark, firewalls, EDR—and knowledge areas like CompTIA Security+, OWASP Top 10, CIA triad, and access control.
How do I optimize my resume to pass ATS for remote cyber security roles?
Use a simple, single-column layout with no tables or images. Extract 8–12 key skills, tools, and tasks from each job description and mirror them honestly in your Summary, Skills, and Projects sections. Aim for at least an 80% keyword match so ATS systems correctly recognize your cyber security experience.
Do I need a degree to get remote cyber security jobs, or is Security+ enough?
Many entry-level and remote cyber security jobs prefer, but don’t strictly require, a degree. According to the ISC2 Workforce Study, the cybersecurity field faces a significant talent shortage, creating opportunities for candidates without traditional degrees. A relevant degree plus Security+ is strong, but candidates can still break in with solid IT experience, Security+ (or equivalent), and a clear portfolio of SOC-style labs and projects that show real, job-aligned skills.
Recommended Reads
